Introducing the Payment Card Industry Data Security Standard (PCI DSS) v4.0.
On March 31, 2022, the Payment Card Industry Security Standards Council (PCI SSC) published an update to its global security standards for protecting account data. Released almost four years after its predecessor, PCI DSS 3.2.1, this latest version introduces new structures, evolving requirements, and updated guidelines.
In this article, we explain the impact PCI DSS v4.0 will have on different organizations, and how to measure and accelerate your own compliance progress.
Watch our LinkedIn Live session for a first-hand account of managing PCI DSS compliance.
4 goals of PCI DSS v4.0
PCI DSS v4.0 heralds the next evolution in payment security, designed to bring the globally accepted standard up to speed with today’s emerging threats and technologies.
More than 6,000 items of feedback and 200 companies contributed to the development of the new standard. Based on these real-world insights, PCI DSS v4.0 outlines its four main goals:
1. Continue to meet the security needs of the payment industry
Why it’s important: Evolves security processes to protect against emerging threats
Examples:
- Expanded multi-factor authentication requirements
- Updated password requirements
- New ecommerce and phishing requirements to address ongoing threats
2. Promote security as a continuous process
Why it’s important: Establishes ongoing security to protect payment data
Examples:
- Clearly assigned roles and responsibilities for each requirement
- Added guidance to help people better understand how to implement and maintain security
3. Add flexibility for different methodologies
Why it’s important: Promotes flexibility and technology innovation in achieving security objectives
Examples:
- Allowance of group, shared, and generic accounts
- Targeted risk analyses empower organizations to establish frequencies for performing certain activities
- Customized approach, a new method to implement and validate PCI DSS requirements, provides another option for organizations using innovative methods to achieve security objectives.
4. Enhance validation methods and procedures
Why it’s important: Supports transparency and granularity in validation and reporting processes
Examples:
Increased alignment between information reported in a Report on Compliance or Self-Assessment Questionnaire and information summarized in an Attestation of Compliance.
When does PCI DSS v4.0 go into effect?
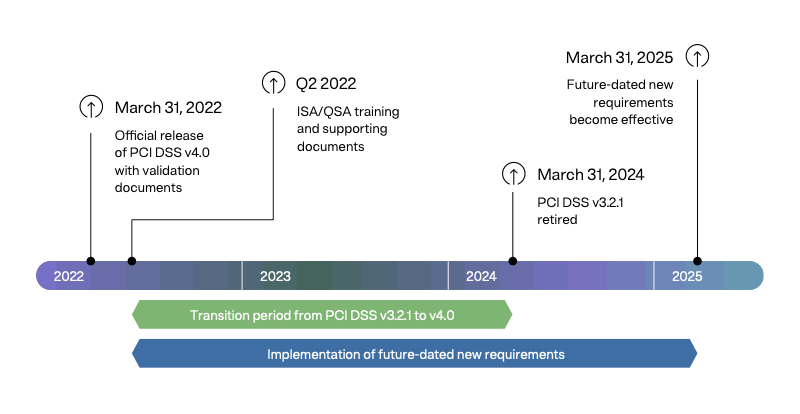
PCI DSS v4.0 is already in effect, following its official release date on March 31, 2022.
Given the significant changes, entities have two years to transition to the new standard.
Here are the important dates to keep in mind:
- March 31, 2022: PCI DSS v4.0 was released
- March 31, 2022 - March 31, 2024: Both PCI DSS v4.0 and 3.2.1 are active and can be used for assessments
- March 31, 2024: PCI v3.2.1 will be retired and entities are given one year to transition to the new standard
- March 31, 2025: Entities must be fully compliant with PCI DSS v4.0