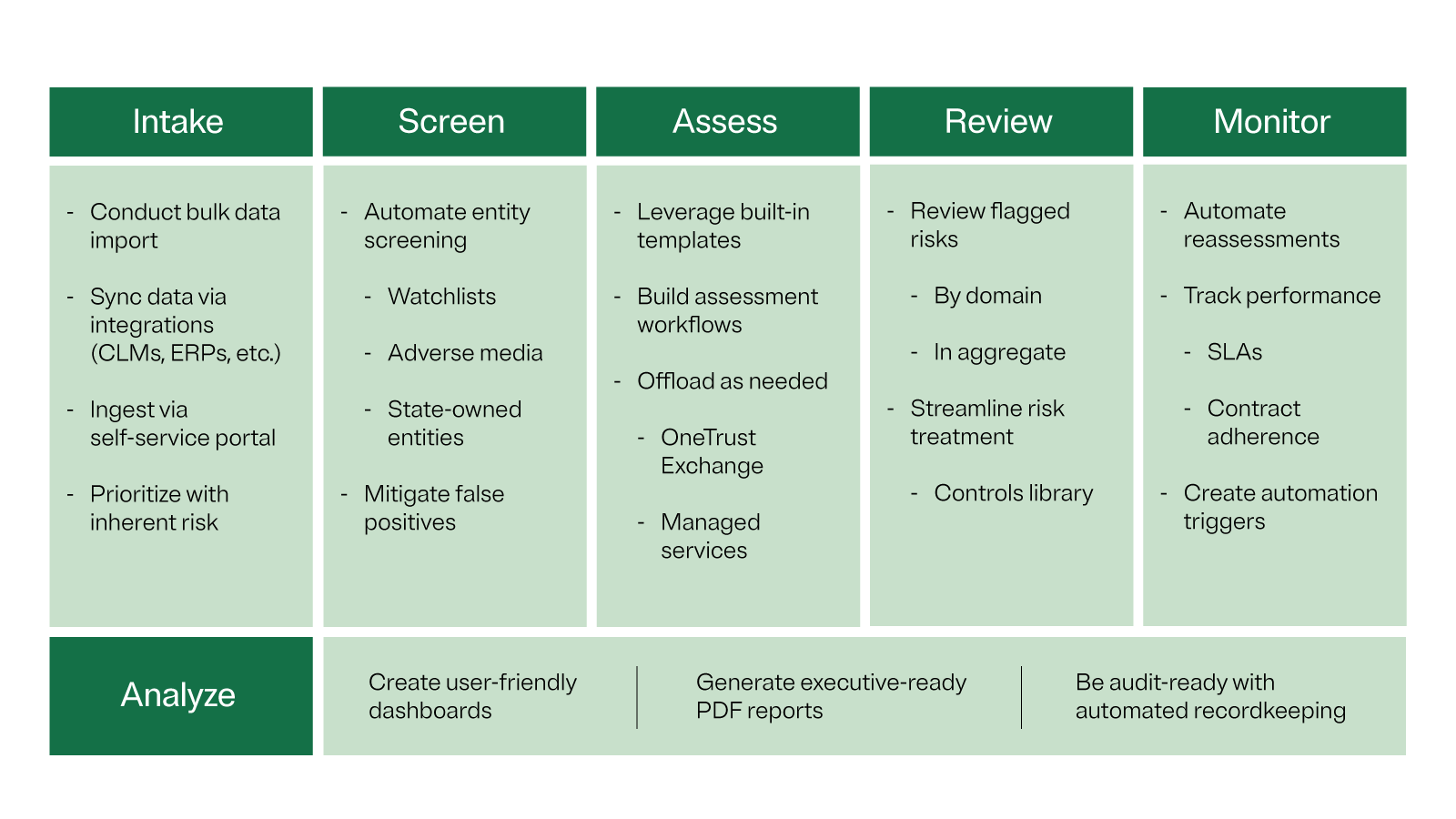
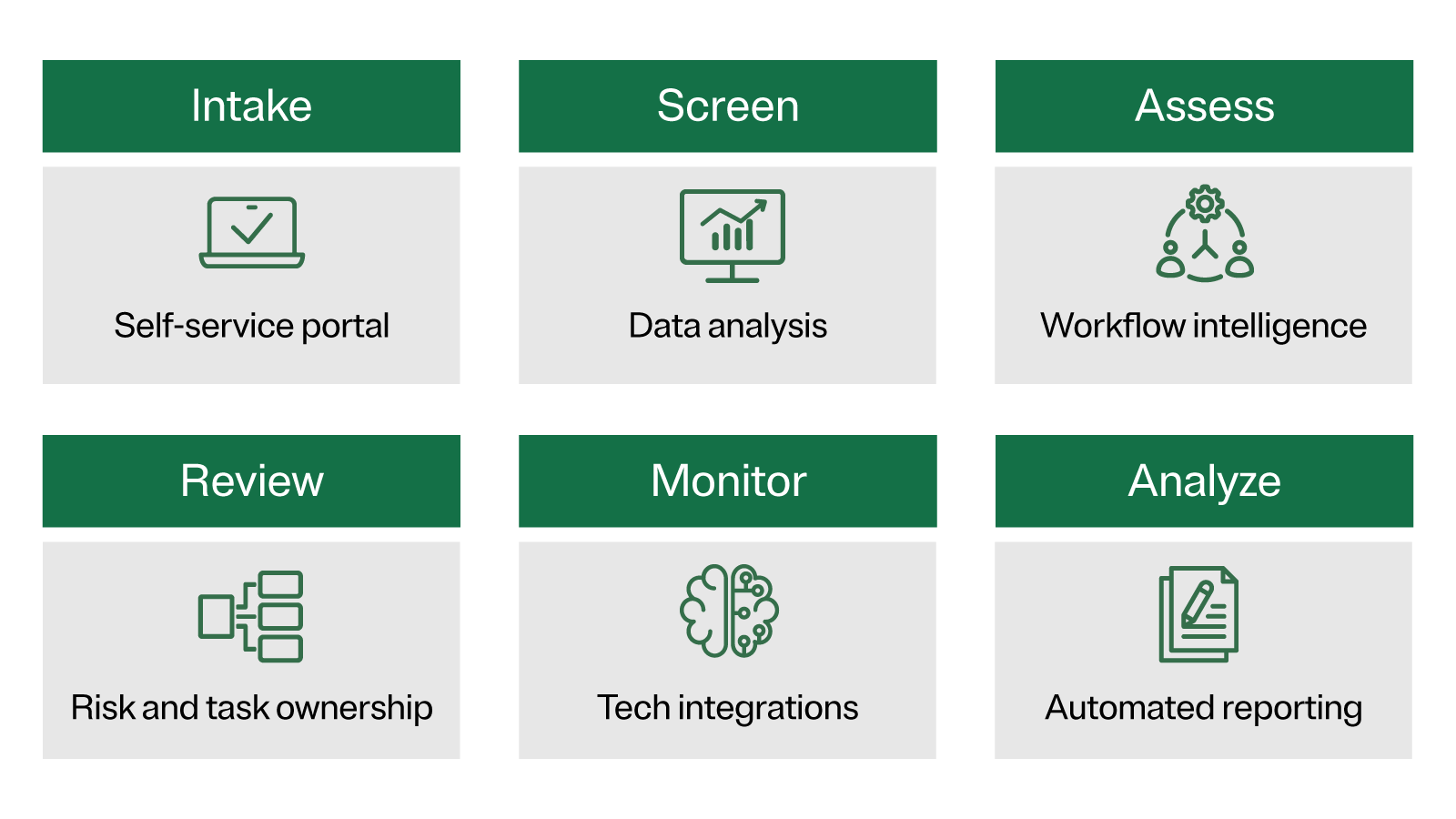
Stage 1: Intake
The first stage focuses on centralizing the collection of all third-party information, which eliminates multiple entry points and potential blind spots further downstream.
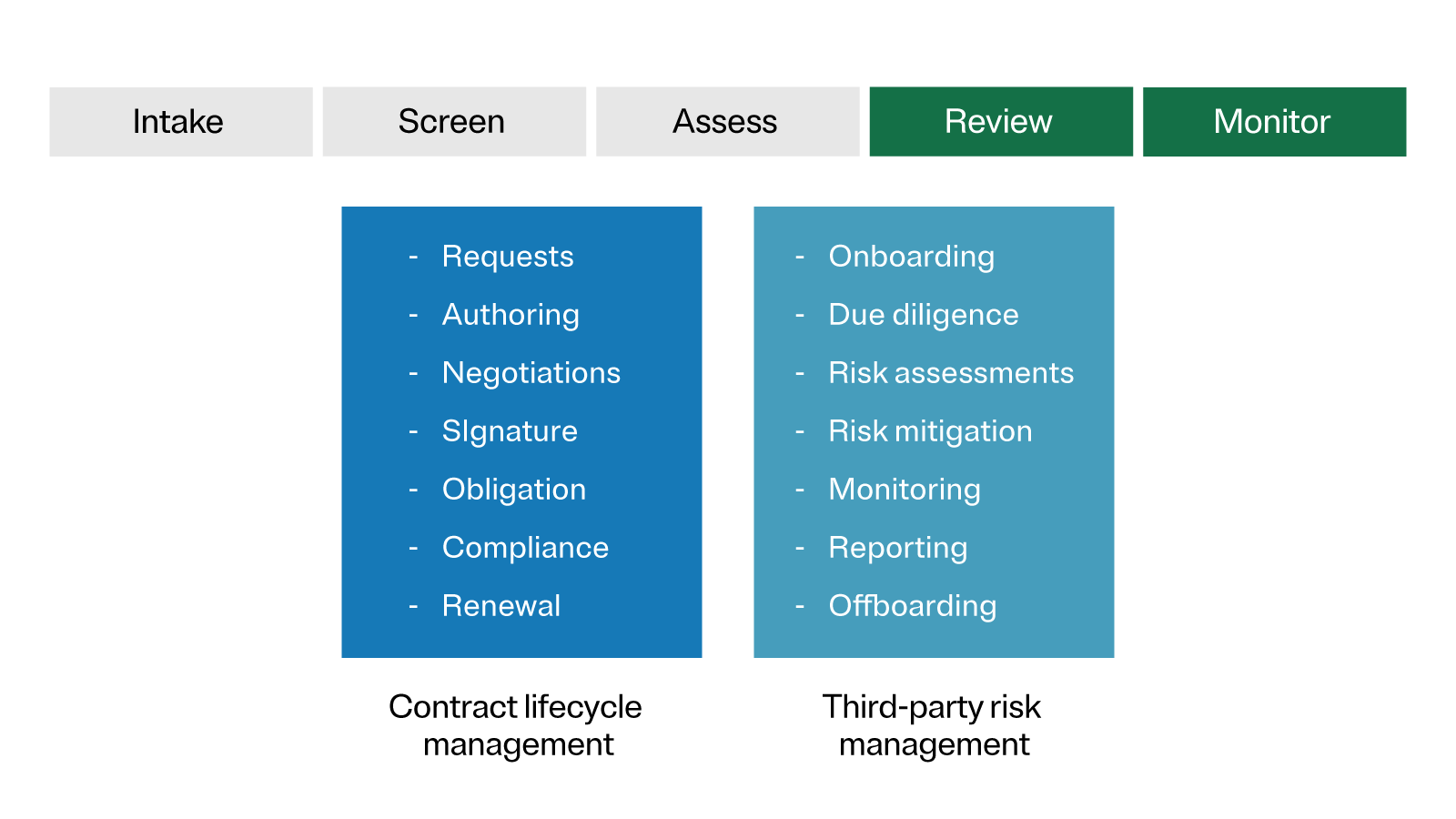
Centralization can be accomplished through a single self-service portal, where employees request the addition of vendors, suppliers, or other parties, or as part of a contract lifecycle management or resource planning tool.
Implementing a self-service intake process gives organizations a head-start on gathering critical third-party information, including privacy certifications, engagement scope, and data types. This helps classify and prioritize third parties from the very beginning, based on their inherent risk to the organization.
Stage 2: Screen
The second stage is to screen and conduct due diligence checks on potential third parties. Some questions to ask during this step include:
- How do we check to make sure this potential third party doesn't have political exposure?
- How do we check for cases of anti-money laundering, anti-corruption, or bribery?
To answer these questions, organizations typically check third parties against sanctions lists, watch lists, or even media sources to identify issues that could pose a high-risk relationship.
In most cases, TPRM will go beyond data privacy and security. It’s important to look at all other types of risks, such as regulatory compliance, ethics, ESG, geopolitics, etc., that can have a potential impact on your operations.
The goal of this step is to uncover any risks associated with the third party and, if your organization still decides to pursue the relationship, to design an appropriate assessment and mitigation approach.
Stage 3: Assess
Out of the entire TPM lifecycle, the assessment stage is the most time- and resource-intensive. It’s also where risk management can be combined with privacy evaluations and other compliance concerns for a more holistic assessment.
Streamline assessments by leveraging dedicated tools that have built-in templates to address various risk domains, including privacy and compliance, data protection, cyber risk, and more.
A third-party risk exchange can also provide pre-validated information to help fact-check the information provided by the third party.
Stage 4: Review
Now it’s time to review all the third-party information and insights collected during the previous stages.
For instance, say a third party that’s under review demonstrates a mature security posture, but is just starting its privacy program. It can’t define whose data it’s collecting, the data elements being collected, and the purpose for data processing. This presents a significant privacy risk to your organization.
Based on these findings, stakeholders can now assign an appropriate risk score and criticality level, and determine the best approach for managing the particular third party.
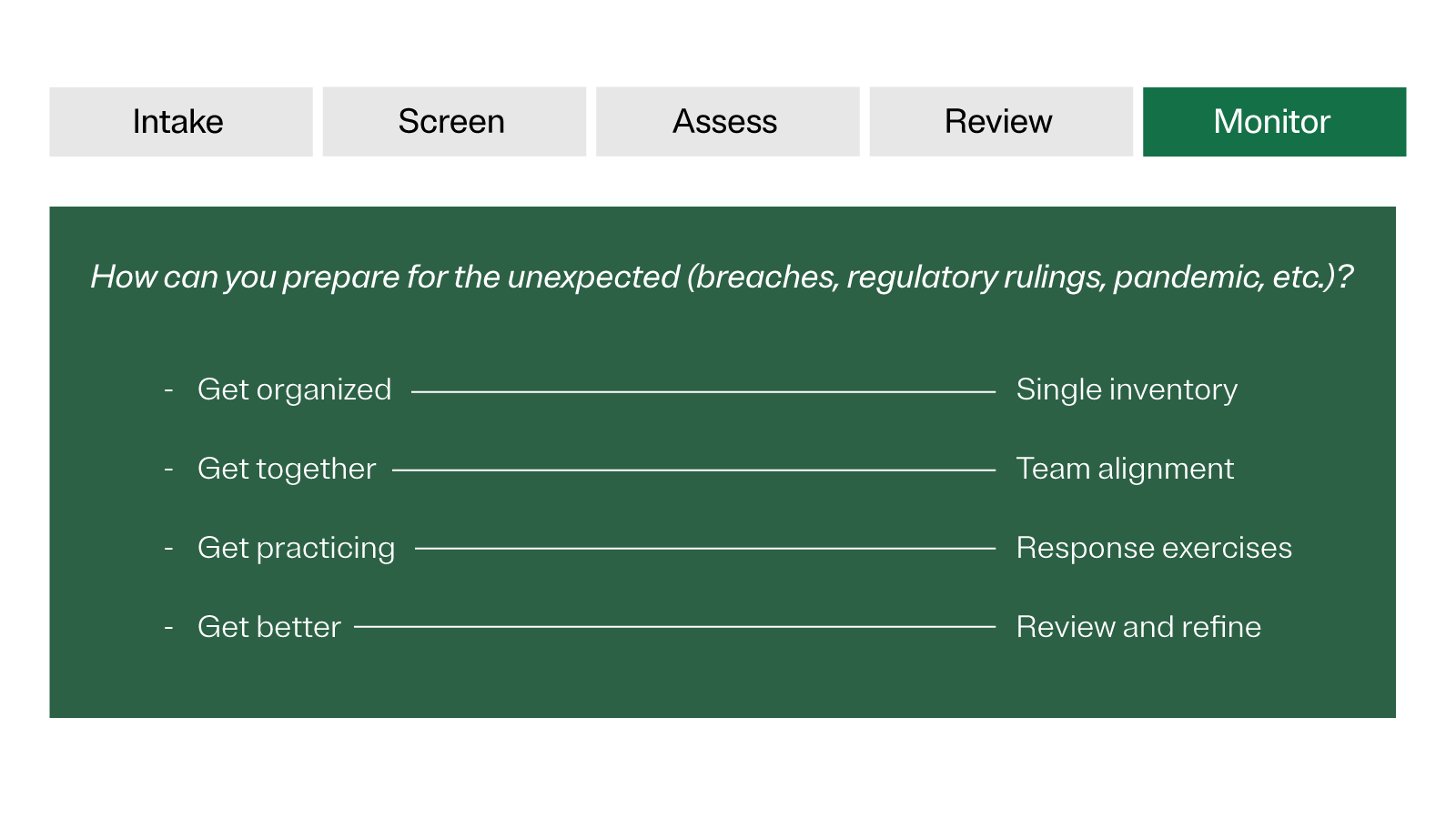
Stage 5: Monitor
As new risks and regulations arise, and a third party’s scope of service evolves, ongoing monitoring is critical to maintaining a healthy relationship.
Effective third-party monitoring typically includes a routine of:
- Assessing specific risk areas.
- Setting a recommended assessment cadence.
- Determining what to include in the questionnaire sent to each third party (based on the specific domains, business scopes, security and privacy compliance).
“In my experience, this stage is where a lot of organizations have a tremendous opportunity to improve efficiency — by automating the ongoing monitoring of third parties,” says Paterson.
5 tips to reduce exposure to third-party risk
As your organization continues to grow its third-party network, it’s necessary to establish a trusted process that identifies risk and reduces exposure across domains.
Here are some of the proven tips to maintain privacy and security compliance at every step of the TPM lifecycle:
Tip 1: Understand where your data is going
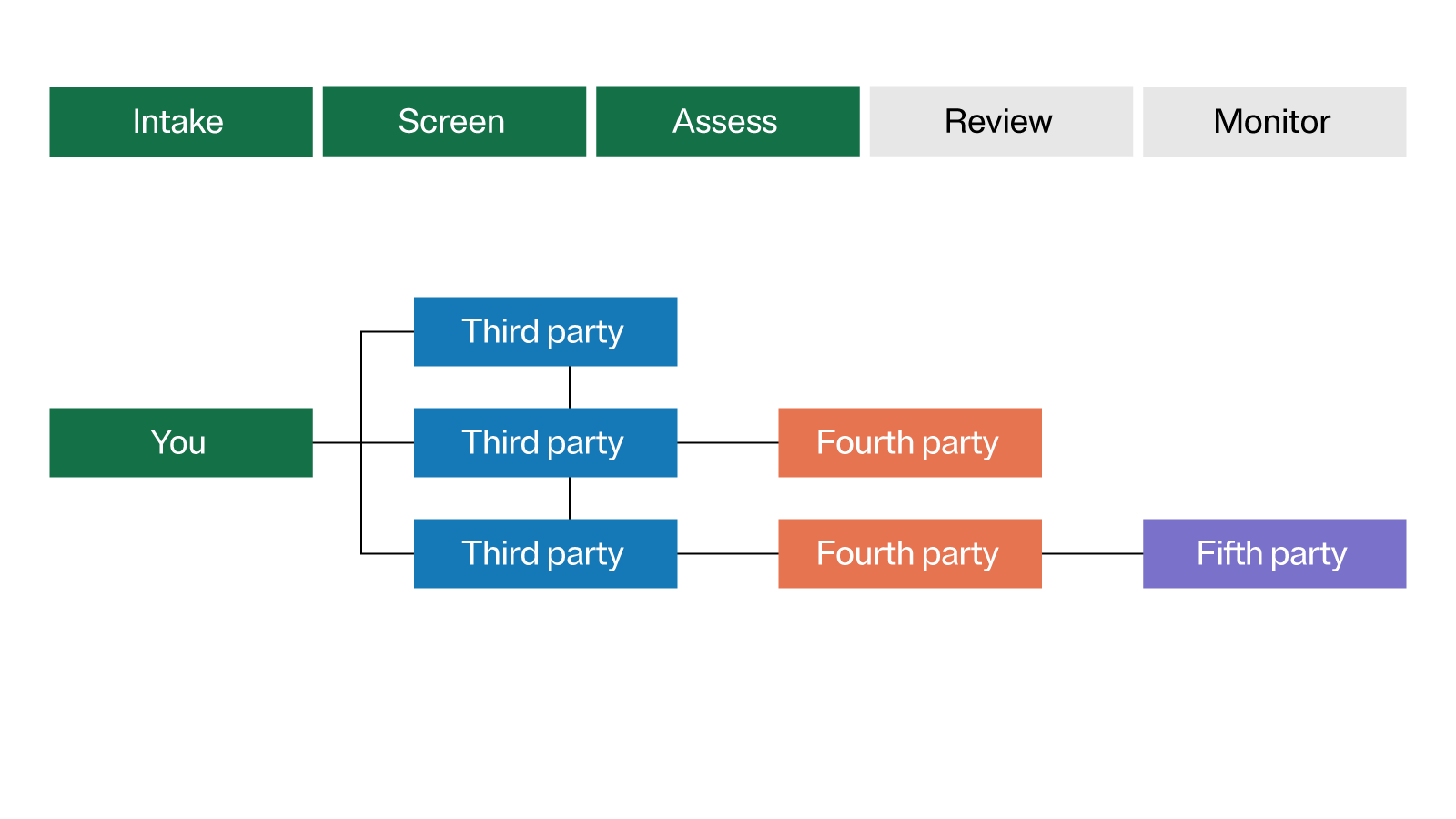
An organization may already manage hundreds or thousands of third parties. But when it comes to personal data, keeping tabs on third-party processes is not enough. You need to track how data moves from the third party to fourth party, to the Nth party, and so on.
For a complete understanding of where your data is going, ask potential third parties about the other parties they use. This is especially critical for complex operations, such as:
- Cross-border data transfers, which often involves additional compliance requirements.
- Third parties with a wide scope of multiple services, as each service may involve different types of data.
- Additions or changes to a third party’s scope that require updates to contracts and assessments.
Build a model that can help teams visualize every step your data takes as it moves between parties (as shown below).